Have you ever experienced situations when you Virtual Machines (VM) were unable to connect to the internet after you have boot it up?
Initially, you probably only have a loopback IP address like the following, well, you are not alone – it happened to me when I was setting up my new Kali Linux or Ubuntu VM as well.
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:56011078 errors:0 dropped:0 overruns:0 frame:0
TX packets:56011078 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:4792283266 (4.4 GiB) TX bytes:4792283266 (4.4 GiB)
You have probably restarted your networking services,
service restart networking
Or performed all kind of different steps, configuring your network, subnet, dhcp, etc information at /etc/network/interfaces but to no avail… you probably have an IP address, but you cannot connect to the internet.
ping: www.google.com: Name or service not known
Today, I am going to share a fix for this issue. It is actually very simple, but it took me a series of troubleshooting before I discover these simple steps to resolve this issue.
Step 1: Simply download the vmnetcfg.exe file, you can easily find an updated copy of the file from the internet. Don’t forget to scan it using virustotal, make it a habit.
By the way, if you are interested, vmnetcfg.exe is a tool which allow users to manage a Windows host computer’s virtual interfaces.
Step 2: Place the vmnetcfg.exe file inside your program files folder.
It is probably located at the default location of “C:\Program Files (x86)\VMware\VMware Workstation” when you installed VMware Workstation to your computer.
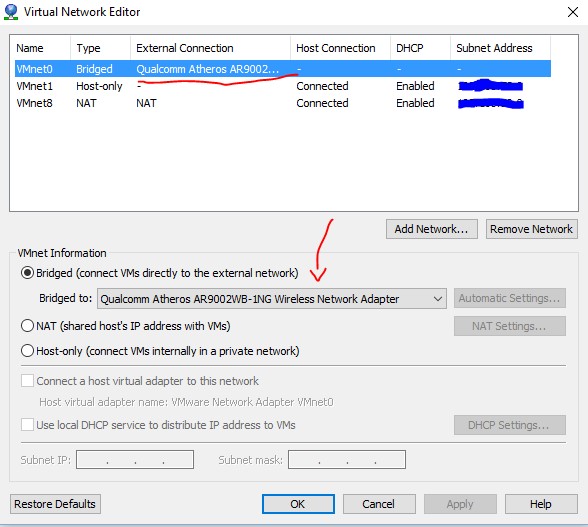
Step 3: Here is the most important part. Run your vmnetcfg.exe file, you will find the following window appearing on your screen.
Look for your VMnet0 or whichever port that is mapped to your machine’s network card, select the option of “Bridged (connect VMs directly to the external network)” and choose your network card in the drop down list. When you are done, click “OK” and there you go, your issue is probably fixed.
Well, I hope that this post has served you well and helped you save some time.