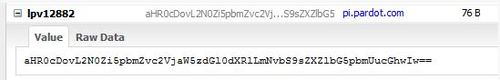
Level 9 shows a login page, the first thing I do is to view the page source… nothing fishy. What about the cookies? Using Firebug, I checked cookies and for a moment, I thought I see something interesting, a cookie named “lpv12882” which contains a base64 encoded string.
However, upon decoding, I see that it is just the page URL of level 9, which is the challenge we are trying to solve now.
Back to square one, but don’t give up just yet. We can always try harder!
Since the login form mentioned the system name, “Cisco IDS Web Login System”, let’s perform a Google search to see what is its default password.
You can easily find websites which shows you the default passwords for various products, in this case, the Cisco IDS. Based on the website, it seems like we can try following default login,
Username: root
Password: attack
We did it! There, we have the key now. But how do we crack it?
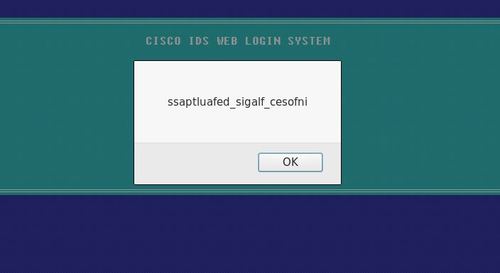
You can try many different methods, trial and error. In this case, if you look carefully, the last 7 letters in the string looks familiar, very familiar… “infosec”, perhaps?
If you run the string “ssaptluafed_sigalf_cesofni” in a string-reverse tool, you will get the flag, “infosec_flagis_defaultpass”
Back to write-up list for InfoSec Institute CTF #1: Hacking for n00bz
Pingback: InfoSec Institute CTF #1: Hacking for n00bz | My Learning Journey