Level goal: The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it
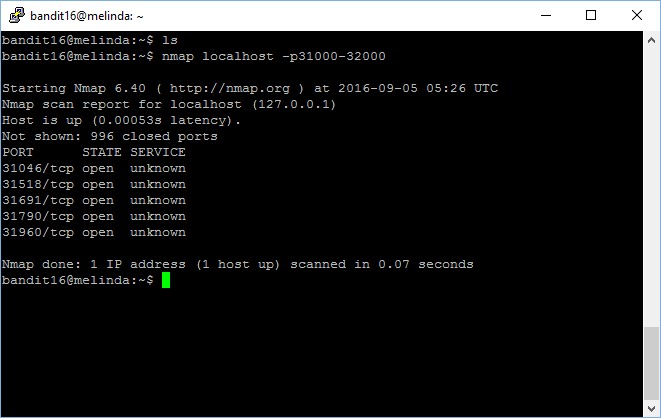
This level require us to have basic understanding in port scanning and identifying the services. First, let’s perform a port scan to identify the open ports between the range of 31000 to 32000.
bandit16@melinda:~$ nmap localhost -p31000-32000 Starting Nmap 6.40 ( http://nmap.org ) at 2016-09-10 14:17 UTC Nmap scan report for localhost (127.0.0.1) Host is up (0.00088s latency). Not shown: 996 closed ports PORT STATE SERVICE 31046/tcp open unknown 31518/tcp open unknown 31691/tcp open unknown 31790/tcp open unknown 31960/tcp open unknown Nmap done: 1 IP address (1 host up) scanned in 0.07 seconds
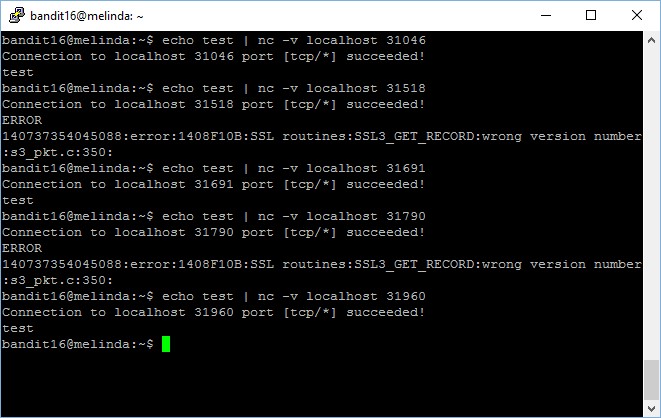
Now there we have shortlisted only 5 ports with services, we will test if it is configured to accept normal connectivity or restricted to only SSL connectivity. For instance, we can do it using the following command,
bandit16@melinda:~$ echo test | nc -v localhost 31046 Connection to localhost 31046 port [tcp/*] succeeded! test
We see that port 31046 is able to accept non-SSL connection, which means that this is not our target. Let’s check out the other 4 ports as well.
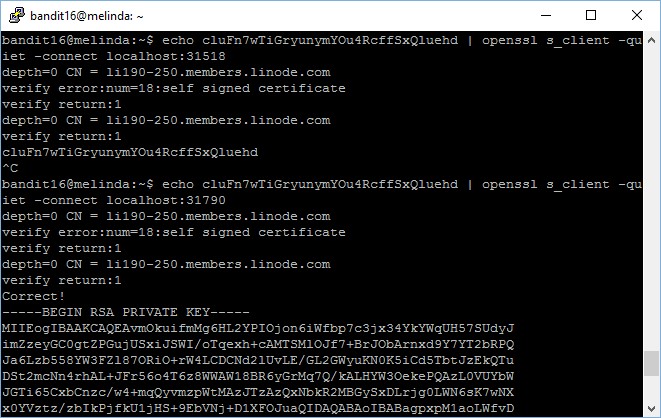
Now, we will focus on the 2 ports which produced error output because they are configured to restrict connectivity to SSL only. We will now try to connect using openssl with s_client option, to check if there is any correct output.
bandit16@melinda:~$ echo cluFn7wTiGryunymYOu4RcffSxQluehd | openssl s_client -quiet -connect localhost:31790
depth=0 CN = li190-250.members.linode.com
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = li190-250.members.linode.com
verify return:1
Correct!
{ ... RSA PRIVATE KEY ... }
The private key for accessing the next level is stored in port 31790! Now, I have to save this RSA private key into a file and then use it to connect to the next level.
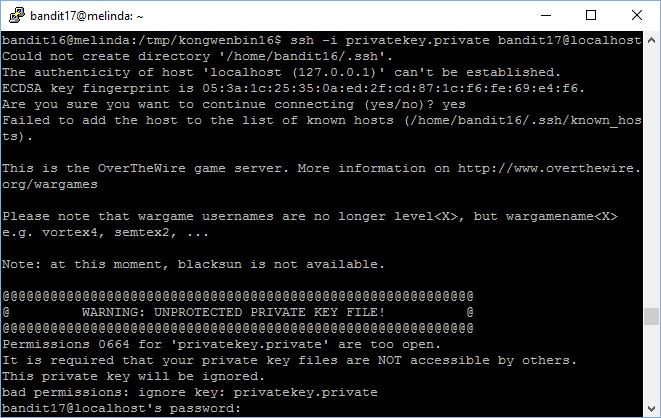
After you’re done with the “copy and paste”, try to connect, you should encounter an error message, which is a good learning point with regards to RSA keys permissions,
The fix is very simple, simply modify the file permission and set it as 400 and you are good to go!
There you go, you are in!

Pingback: OverTheWire: Bandit Write-up | My Learning Journey