Level goal: A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed
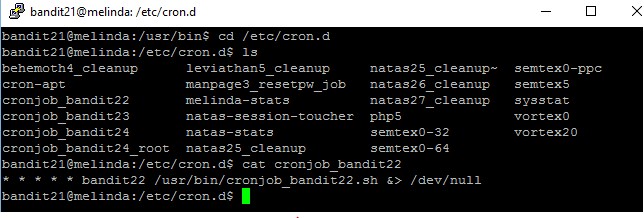
This level is very simple, as hinted by the clue, just navigate to the /etc/cron.d directory and look for the files, you will noticed the cronjob_bandit22 files.
When opened to view the content of the cronjob, it seems that the job basically triggers a script located at /usr/bin/cronjob_bandit22.sh
To more accurately grep the files and read its content, we can perform the following grep,
ls -l | grep cronjob
Below are the list of files.
Since cronjob_bandit22.sh is the only file which is related to this level, let’s view its content.
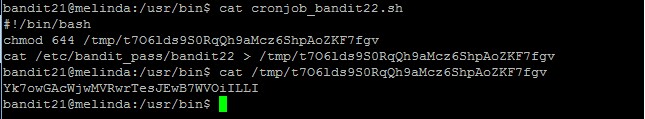
bandit21@melinda:/usr/bin$ cat cronjob_bandit22.sh #!/bin/bash chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Now we know that the password is stored in the /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
bandit21@melinda:/usr/bin$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
The password to gain access to the next level is Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI.
Pingback: OverTheWire: Bandit Write-up | My Learning Journey