Level goal: There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
NOTE: To beat this level, you need to login twice: once to run the setuid command, and once to start a network daemon to which the setuid will connect.
NOTE 2: Try connecting to your own network daemon to see if it works as you think
In this level, basically we need to setup a listener service to listen on any port, and then use the binary submit this level’s password to it. If It is correct, it will provide the password to the next level.
First, let’s check what are the ports opened.
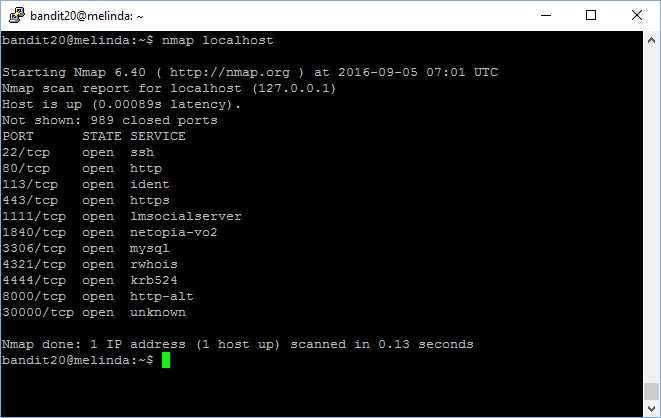
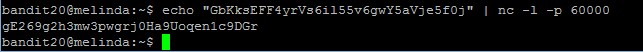
Now you setup your own listener which echo the current level password when any clients connected.
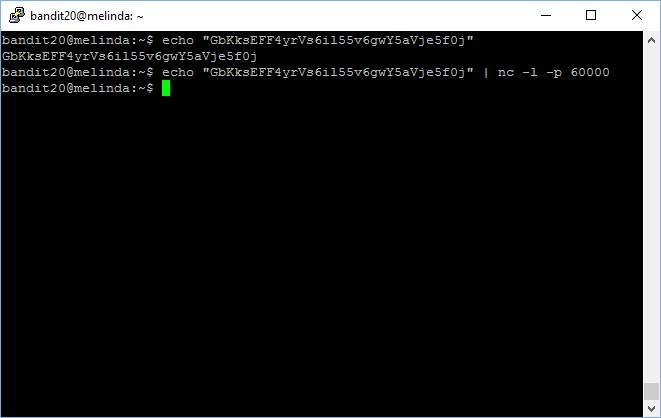
Now you setup another terminal and try to check if the service is there (of course it will be there) and perform testing by trying to connect,
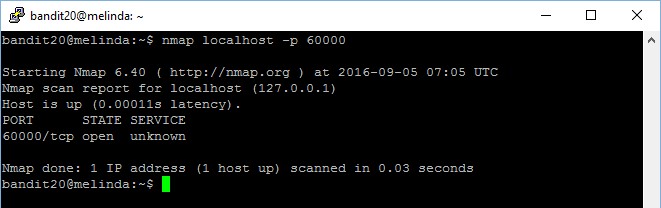
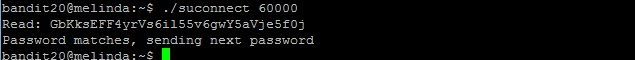
Notice that nmap port scan has detected the service at port 60000 which you have set up in the other terminal? Now, use the suconnect binary to establish connectivity to port 60000
Password matches, now the next password is sent to the server listener.
The password to gain access to the next level is gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr.
Pingback: OverTheWire: Bandit Write-up | My Learning Journey
Salty
October 24, 2019Thanks for all of this. Confused though — when I follow your instructions and try to set up the listening service as follows —
bandit20@bandit:~$ echo “GbKksEFF4yrVs6il55v6gwY5aVje5f0j”
GbKksEFF4yrVs6il55v6gwY5aVje5f0j
bandit20@bandit:~$ echo “GbKksEFF4yrVs6il55v6gwY5aVje5f0j” | nc -l -p 60000
It does not respond with a new prompt but seems to hang. I have to ctrl+c to get a prompt.
Then, when I check the port in a separate terminal window, it shows that service as closed. (I’m using Putty on a windows 10 laptop, if that helps.)
bandit20@bandit:~$ nmap localhost -p 60000
Starting Nmap 7.40 ( https://nmap.org ) at 2019-10-24 09:19 CEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00012s latency).
PORT STATE SERVICE
60000/tcp closed unknown
Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds
bandit20@bandit:~$
Salty
October 24, 2019For whatever reason, the command worked when I did NOT put the pwd inside double quotes, just straight ahead. Thx
kongwenbin
August 17, 2021Hi Salty, so sorry for the late reply, I see you have figured out the solution by yourself already, cool 🙂