Level goal: To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used to setuid binary.
In this level, we will be working on a file which has its setuid set.
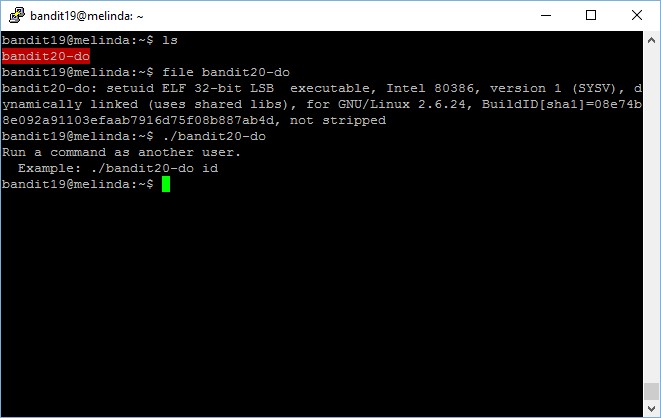
bandit19@melinda:~$ file bandit20-do bandit20-do: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=08e74b8e092a91103efaab7916d75f08b887ab4d, not stripped
It’s interesting because it allows us to run a command or do anything as bandit20.
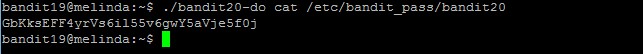
bandit19@melinda:~$ ./bandit20-do Run a command as another user. Example: ./bandit20-do id bandit19@melinda:~$ ./bandit20-do cat /etc/bandit_pass/bandit20 GbKksEFF4yrVs6il55v6gwY5aVje5f0j
The password to gain access to the next level is GbKksEFF4yrVs6il55v6gwY5aVje5f0j.
Pingback: OverTheWire: Bandit Write-up | My Learning Journey