At first look, level 11 seems to be related to something specific to PHP scripting because it shows a very big PHP logo.
After taking a careful look, the PHP logo looks different from the original logo. Moreover, if you read the page source, you will noticed that the PHP logo is named as “img/php-logo-virus.jpg”. Why name the file as virus?
Just to be sure, let’s run it using the file command to identify what kind of file is it. In my Linux system, I run the file command:
file php-logo-virus.jpg
And below is the output:
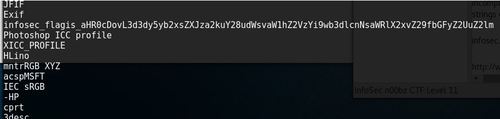
php-logo-virus.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 96×96, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=6, name=infosec_flagis_aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9w], baseline, precision 8, 450×237, frames 3
Did you see it? It says “infosec_flagis_aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9w”
Running the encoded portion of the string through a base64 decoder tool will give you the following URL – “http://www.rollerski.co.uk/imagesb/p”, which essentially leads to an Error 404, page not found.
My logic – since the string turned out of be quite legit, yet the URL points to nothing. Probably the URL is incomplete. Therefore to verify this, we can run a strings command on the file to see what are the existing strings contained in the file.
strings php-logo-virus.jpg
Below is the output,
True enough, the string we gotten earlier was incomplete. Now we have the complete string:
infosec_flagis_aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9wb3dlcnNsaWRlX2xvZ29fbGFyZ2UuZ2lm
Let us put it through the base64 decoder tool again – there, it returns an image file – http://www.rollerski.co.uk/imagesb/powerslide_logo_large.gif
As strange as it seems to be, this is the flag for level 11, “infosec_flagis_powerslide”
Back to write-up list for InfoSec Institute CTF #1: Hacking for n00bz

Pingback: InfoSec Institute CTF #1: Hacking for n00bz | My Learning Journey
Pingback: The WEDA Coalition