Hacksplaining is one of the best website that I have seen so far in terms of the way it teaches people about web vulnerabilities. It uses a very simple and fun way of teaching people about the concepts and theory of web vulnerabilities. To make the deal even better, it is free. I don’t know who are the folks behind this website, but I really like how they make education seems so fun. Kudos to them for the amount of time they have invested in coming out with all those examples and exercises, and etc.
Also, I really like their tagline,
“learn to hack, learn to protect yourself”
I fully agree with it, just like when you play sports, you need to know the rules and the various techniques and tactics that can be deployed during an attack, before you are able to effectively defend against them. Same concept applies here, if you don’t understand cross site scripting or SQL injection, how are you supposed to ensure that your web application is protected against them?
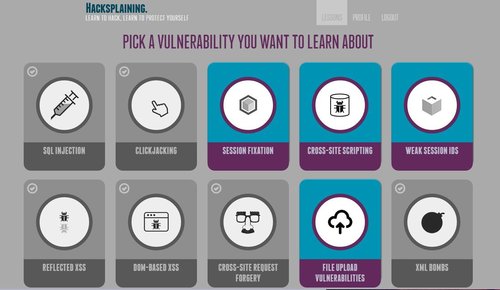
The following are the list of techniques that you can learn through Hacksplaining‘s interactive way of teaching you web vulnerabilities,
- SQL Injection
- Clickjacking
- Session Fixation
- Cross-Site Scripting
- Weak Session IDs
- Reflected XSS
- Dom-Based XSS
- Cross-Site Request Forgery
- File Upload Vulnerability
- XML Bombs
- Open Directs
- User Enumeration
- Broken Access Control
- Unencrypted Communication
- XML External Entities
- Information Leakage
- Password Mismanagement
- Privilege Escalation
- Command Execution
- Directory Traversal
Check it out: Hacksplaining: Learn to Hack