The password for the next level is stored in a file called – located in the home directory
As the hint has suggested, you need to check the content in the file named – (a dash symbol) to obtain the password to access level 2.
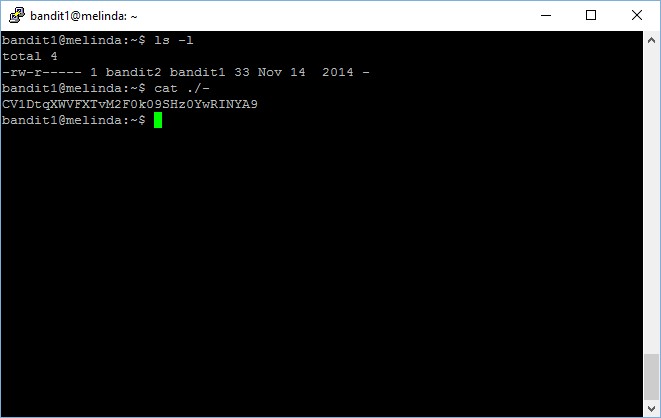
However, if you just simply run the cat command to view print the content in the file named – (a dash symbol), your terminal is just going to get stuck,
When cat sees – (a dash symbol) as a filename, it treats it as a synonym for stdin. To avoid getting treated as a stdin and have your terminal getting nowhere, you need to provide the full path of the file instead of simply cat the file name.
bandit1@melinda:~$ cat ./- CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
The password to gain access to level 2 is CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9