Following up from my previous post regarding the InfoSec Institute: Capture the Flag (CTF), I hope the resources are helpful to you. There are many more resources out there, thanks to the very supportive community of information security professionals and enthusiasts who enjoy sharing their knowledge to help one another.
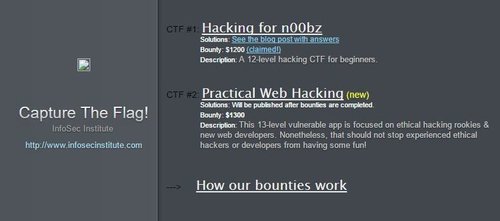
Today, I would like to introduce the CTF challenges created by Infosec Institute – they provides entry-level CTF challenges for beginners to learn and play. To make things even better, they also giveaway some small token of monetary appreciation to participants who are able to complete all the challenges AND do a write up on the solutions or helpful instructions to help other participants whom are stuck.
I find that this is a very smart way of getting people to contribute to the information security community, to get them started. A write up can be simple, just provide some steps to help people get through and learn something along the process. In fact, you learn more when you start writing (it keeps you thinking!).
In case you missed the link above, you can try out the challenges here: http://ctf.infosecinstitute.com/
