Level goal: The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
This level is one of the most tedious stage in this CTF challenge. First, let’s move the file to a new directory in the /tmp folder under your name (create one using the mkdir command!).
Now we have to perform a reverse hashdump using xxd command,
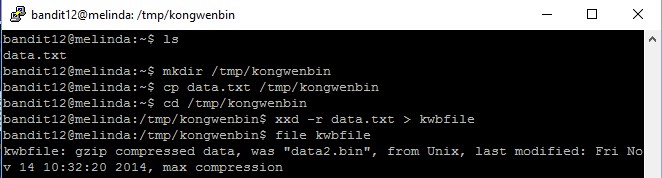
bandit12@melinda:/tmp/kongwenbin12$ xxd -r data.txt > kwbfile
After performing the reverse hashdump command and writing the output to a file (in my case, I have named it “kwbfile”), run the file command to check what kind of file is it.
bandit12@melinda:/tmp/kongwenbin12$ file kwbfile kwbfile: gzip compressed data, was "data2.bin", from Unix, last modified: Fri Nov 14 10:32:20 2014, max compression
From here onwards, the flow goes like this,
- Identify what type of file is this, using the file command
- Rename it to that particular file format, using the mv command to change its file type
- Decompress/unzip the files using the correct type of tool
- Repeat the above process until you have the file
The following is a dump of the commands I have, it will be quite lengthy. However, it basically follows the flow which I described above. I have added a “line break” after each change in file type, to make it easier to follow. I hope it helps!
Scroll to the bottom for the password to gain access to the next level.
bandit12@melinda:/tmp/kongwenbin12$ file kwbfile kwbfile: gzip compressed data, was "data2.bin", from Unix, last modified: Fri Nov 14 10:32:20 2014, max compression bandit12@melinda:/tmp/kongwenbin12$ mv kwbfile kwbfile.gz bandit12@melinda:/tmp/kongwenbin12$ gzip -d kwbfile.gz bandit12@melinda:/tmp/kongwenbin12$ file kwbfile kwbfile: bzip2 compressed data, block size = 900k bandit12@melinda:/tmp/kongwenbin12$ mv kwbfile kwbfile.bz2 bandit12@melinda:/tmp/kongwenbin12$ bzip2 -d kwbfile.bz2 bandit12@melinda:/tmp/kongwenbin12$ file kwbfile kwbfile: gzip compressed data, was "data4.bin", from Unix, last modified: Fri Nov 14 10:32:20 2014, max compression bandit12@melinda:/tmp/kongwenbin12$ mv kwbfile kwbfile.gz bandit12@melinda:/tmp/kongwenbin12$ gzip -d kwbfile.gz bandit12@melinda:/tmp/kongwenbin12$ file kwbfile kwbfile: POSIX tar archive (GNU) bandit12@melinda:/tmp/kongwenbin12$ mv kwbfile kwbfile.tar bandit12@melinda:/tmp/kongwenbin12$ tar xvf kwbfile.tar data5.bin bandit12@melinda:/tmp/kongwenbin12$ file data5.bin data5.bin: POSIX tar archive (GNU) bandit12@melinda:/tmp/kongwenbin12$ mv data5.bin data5.tar bandit12@melinda:/tmp/kongwenbin12$ tar xvf data5.tar data6.bin bandit12@melinda:/tmp/kongwenbin12$ file data6.bin data6.bin: bzip2 compressed data, block size = 900k bandit12@melinda:/tmp/kongwenbin12$ mv data6.bin data6.bz2 bandit12@melinda:/tmp/kongwenbin12$ bzip2 -d data6.bz2 bandit12@melinda:/tmp/kongwenbin12$ file data6 data6: POSIX tar archive (GNU) bandit12@melinda:/tmp/kongwenbin12$ mv data6 data6.tar bandit12@melinda:/tmp/kongwenbin12$ tar xvf data6.tar data8.bin bandit12@melinda:/tmp/kongwenbin12$ file data8.bin data8.bin: gzip compressed data, was "data9.bin", from Unix, last modified: Fri Nov 14 10:32:20 2014, max compression bandit12@melinda:/tmp/kongwenbin12$ mv data8.bin data8.gz bandit12@melinda:/tmp/kongwenbin12$ gzip -d data8.gz bandit12@melinda:/tmp/kongwenbin12$ file data8 data8: ASCII text bandit12@melinda:/tmp/kongwenbin12$ cat data8 The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
The password to gain access to the next level is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL.