Level goal: A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints
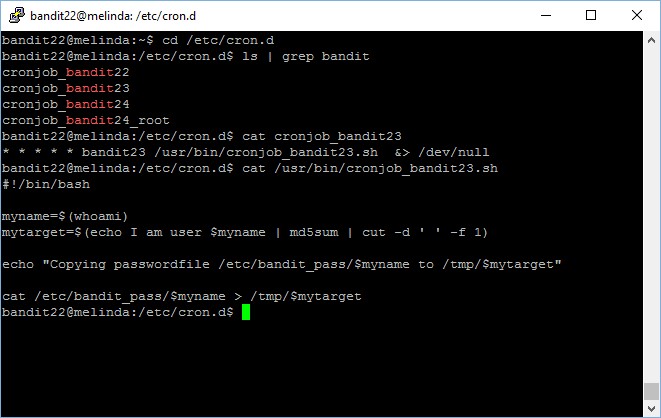
Like what we have done in the previous level, let’s navigate to the /etc/cron.d path and check the cronjob files.
Notice that cronjob_bandit23 is will be running the /usr/bin/cronjob_bandit23.sh script? Let’s view its content.
bandit22@melinda:/etc/cron.d$ cat /usr/bin/cronjob_bandit23.sh #!/bin/bash myname=$(whoami) mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1) echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget" cat /etc/bandit_pass/$myname > /tmp/$mytarget
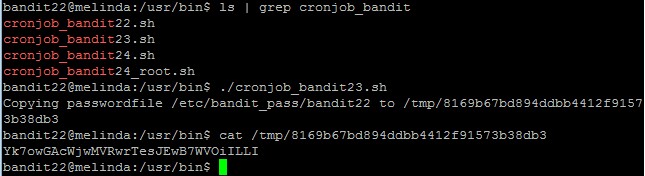
Yes, you have guessed correct. When this script is being run, it will write the currently logged-on user’s password into a file.
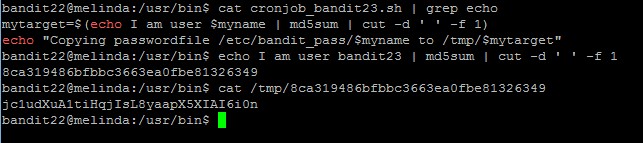
The file name is basically a md5 hash of “echo I am user bandit22 | md5sum | cut –d ‘ ‘ –f 1”
Since we need the password of bandit23, let’s manually run the hash and use its hash as the directory name. The password might be there, provided that someone with the bandit23 credentials has already ran this script (they probably have).
The password to gain access to the next level is jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n.
Pingback: OverTheWire: Bandit Level 23 to Level 24 | My Learning Journey
Pingback: OverTheWire: Bandit Write-up | My Learning Journey