Last week, I attended the RSA Conference 2016 Asia Pacific & Japan which was held at Marina Bay Sands (MBS), Singapore. It was a pretty enriching experience as I get to not only hear directly from various security vendors about how their products are beneficial to the industry, but also get to attend keynote sessions with top-rated speakers in the information security industry.

There were many security vendors in the Sands Grand Ballroom level 5 with their respective booths being setup with their newest products. Each booths run their own product demonstration in every 1 or 2 hours intervals. Can see that most of the presenters are pretty enthusiastic in sharing their products’ new features.

To see the full list of exhibitors which have setup a product demonstration booth to share about their products, you can check out this link.
There were also some companies which also gotten a place to share about their products in an open area called the Demo Theatre. It is like a mini stage with a number of chairs. Unfortunately, there were not many attendees. I’m glad I attended a few sessions though and learnt quite a bit about how an enterprise can incorporate various types of products to improve on their security defenses to protect their company’s information and data.

Check out the full list of sessions at the Demo Theatre on this link.
Moving on to the best part of the event, the keynote sessions. Having attended the session on 21 July 2016, I sat in for all 4 of the keynote sessions.

First off is the “Security in the World-Sized Web” by Bruce Schneier. He came to raise the awareness to the information security experts in the industry about the uprising of IoT (Internet of Things) world-wide robots. These IoT devices are collecting information for a purpose, just like what robots are doing. These increased usage and coverage of IoT devices will not only give power to defenders, but also the attackers. He is suggesting for smart government involvement in this area, as he believe that regardless of whether we desire for it, government are going to be part of this. Therefore, the better way of involvement is to be involved “smartly”. And lastly, policy makers need to know about the technology, which is probably, not necessarily the case in today’s industry, and this have to be changed.
Next up is the “Business Defence – Managing the Insider Threat with Security Analytics” by Alex Taverner. He talks about how insider threat has always been an issue with companies, but it is remained largely neglected in the defensive security industry. He proposed a solution from his company (or any other company, if any) which could allow an enterprise to make use of various data sources to identify insider threats, such as the social media and the behavior of the employees. I feel that while this is something interesting and definitely helpful to a large company, the collection of data is something very difficult to be implemented. Even if it is implemented forcefully, it may not be enforced and thus, practical. Without accurate data, given the best formula and analytic tools, the results would not be beneficial, do you not agree?
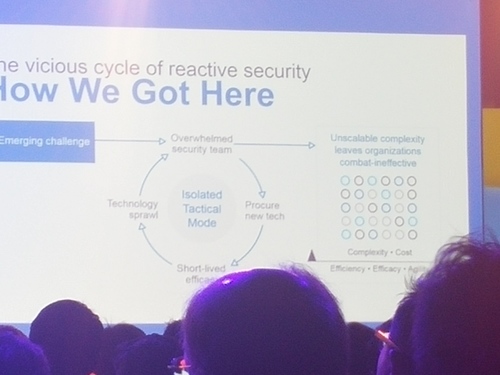
Moving on to “Maximize the Value of Your Threat Intelligence” by Jason Rolleston. He discussed about the topic of effective protection, which is something I strongly agreed. A large company can definitely invest in all the newest technologies and software, but how well do they truly integrates? Check out the image above, this is a very true situation in many companies which I have come across either personally or understood through my contacts. Allow me to put them into text,
Emerging challenge will lead to an isolated tactical mode, where the challenge overwhelm the security teams of a large corporation. The management team will then invest in the procurement of a new technology or products without proper evaluation on how well they could integrate with the existing systems. After much struggling and a long time taken, they finally managed to complete the integration with various implementation design flaws here and there, which lead to a short-lived efficiency. After a number of such scenarios have taken place in the company, it will lead to technology sprawl where once again, the vicious cycle of security team being overwhelmed will take place again. Management need to have the far sight and try to understand the technology instead of blindly follow the trend and keep investing without planning.

Lastly, we have the “How to Build a World-Class Network Defence Organization” by Chris Coryea. This man gives an aura of confidence, the entire speech really leaves a strong impression to me. He shared a lot of real life examples on how a corporation can build a strong network defense through various key areas. The only complaint that I have is that he focuses too strongly on his company’s product, other than that, I really like his session. In fact, allow me to share one of the statements which he shared during his session, which I like the most, and fully agreed upon (with both hands),
Technology can be taught, the framework can be integrated – but focusing on the analytical mindset is the common thread for building an effective team.
In short, to build the best security defense team, you don’t necessarily need people who have “computer science” background or “master in forensics” in their CV or resume, what you need is people with a strong passion and hunger to solve tough problems.