For a bounty of $40, level 4 shows a very cute cookie monster image with the text “HTTP means Hypertext Transfer Protocol”.
When hovering your mouse over the image, it gives a pop-up text saying “stop poking me”. Now, that is quite a hint. The pop-up message is trying to tell us that there is nothing with the image, to obtain the flag, we should focus on HTTP’s element itself.

So, who is in the image? Cookie monster? Let’s look at the list of cookies on the page… bingo! There is a suspicious looking cookie, called fusrodah.
People who have played the game “Elder Scrolls V: Skyrim” would know what it is. “Fus Ro Dah” is one of the shouts (it’s like the spells/magic in other games) that can be performed in the game, it basically sends out a shockwave to its target to push them back or make them fall. It have since become an internet meme.
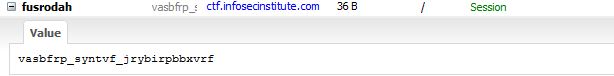
At this point, logically speaking, we have to do some trial and error to see what does “vasbfrp_syntvf_jrybirpbbxvrf” means. However, since the string of text only contains alphabets, it is probably not encoded using an advanced method.
After performing a very simple ROT13 decryption using the ROT13 tool, there we go “infosec_flagis_welovecookies”.
Back to write-up list for InfoSec Institute CTF #1: Hacking for n00bz