Level 13 require us to find the backup file for the challenge. Well, looks like the search for the backup file is the challenge itself.
I tried to navigate to some of the common web pages which I can think of, such as /levelthirteen-backup.php, /levelthirteen_backup.php, /archive.php, /archives.php, /backup.php, /backups.php, and etc., but there seems to be no luck. After that, I read some forums, seems like some people do quick backup based on dates or version, such as /levelthirteen.php.20160520 or /levelthirteen.php.v2.2, and etc.
And then there are also some people who conveniently add a “old” behind the file name… such as /levelthirteen.php.old, which in this case, is the location where the backup of level 13 is stored. Trial and error – checked!
As shared in my previous write-ups, I like to use file and strings on any files which I come across to perform a simple check. And that is exactly what I did.
strings levelthirteen.php.old
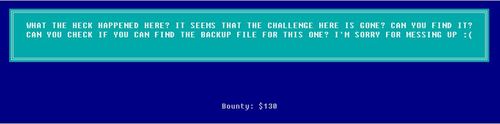
Based on the content of the backup file, we can see a new PHP code snippet which prompts us to download a mysterious file, “misc/imadecoy” – just the same way in the past challenges. I bet you are getting a hang of it by now. Let’s check what is that new mysterious file we just downloaded.
file imadecoy
Below is the output:
imadecoy: tcpdump capture file (little-endian) – version 2.4 (Linux “cooked”, capture length 65535)
Looks like it is a tcpdump capture file. Remember we used Wireshark to open and analyse the pcap file in level 6? Let’s do the same for this file.
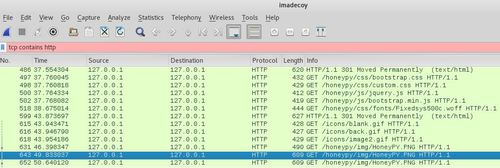
First, you open the file and as you can see, there are a lot of DNS traffic. Let’s look for HTTP traffic by performing a packet display filter,
tcp contains http
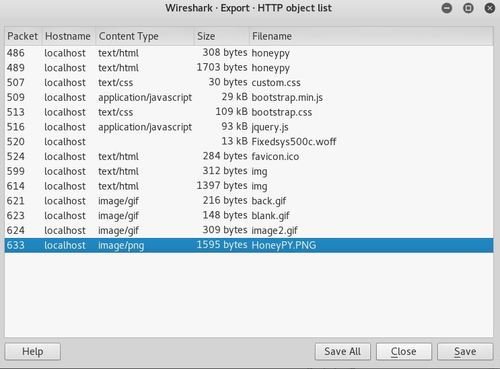
Looks like there are quite a number of files related to honeypy that were transmitted during the tcpdump capture. You will also notice that the source and destination are both 127.0.0.1 / localhost. If that is the case, you cannot go to the same website to see what are the contents. However, you can export the objects. Simply go to “File > Export Objects > HTTP…” and you will see the following prompt,
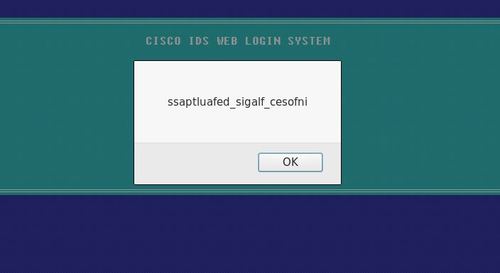
You can choose to save all files and perform further analysis. For level 13, you will only require “HoneyPY.PNG” file as the flag is right in the file, flag is “infosec_flagis_morepackets”
Back to write-up list for InfoSec Institute CTF #1: Hacking for n00bz