Level goal: Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
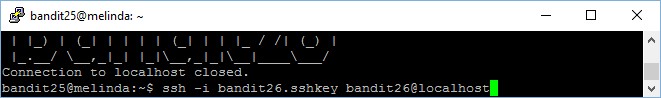
Indeed, logging in is easy, simply run the usual command which allow you to login using SSH key instead of login credentials
ssh -i bandit26.sshkey bandit26@localhost
However, after you logged into bandit26, you will be logged out immediately, “Connection to localhost closed.”
As hinted by the question, let’s take a look at the bash used by bandit26,
bandit25@melinda:~$ cat /etc/passwd | grep bandit26 bandit26:x:11026:11026:bandit level 26:/home/bandit26:/usr/bin/showtext
Instead of /bin/bash, bandit26 is using /usr/bin/showtext, which is apparently not a shell. Let’s look at the content of the file
bandit25@melinda:~$ cat /usr/bin/showtext #!/bin/sh more ~/text.txt exit 0
The way to obtain the password for this level is extremely creative, I salute the team who designed this portion of the challenge, it’s really good.
As we know, we will be logged out immediately after we gain access to the server using the SSH key. The way to get the level 27 password is to gain access to the file before your shell gets terminated.
Think about it, how can that be possibly done? The hint is that you are able to “log in” to the system, just that when it spawns a shell, it terminates the shell immediately – the exact code is “exit 0” as we have see in the showtext “shell”.
Here’s the solution:
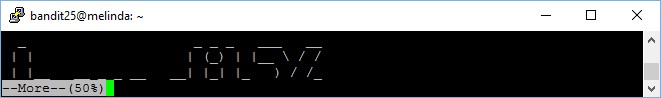
First, minimize your terminal so that when you are logged into bandit26 via ssh command, the large “bandit26” ASCII art banner will force a “more” message to prompt you to continue the output. You may refer to the screenshot as an illustraton of how I have minimized my terminal,
ssh -i bandit26.sshkey -t bandit26@localhost cat text.txt
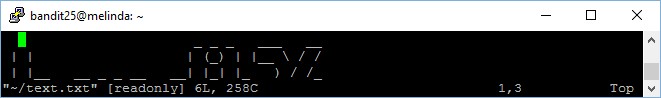
Now that you have forces the terminal to prompt you to continue the display via “more” or “–More–(50%)” in this case, press “v” to enter “vim”, a built-in text editor on Unix machines. You will see the output as per below,
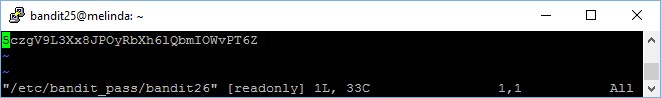
Now, press “:e /etc/bandit_pass/bandit26” to edit the password file of bandit26.
There you go, you have the password to proceed to level 27!!
Let’s review what we have done. We have forces the terminal to display a “more” output, where we can open a VIM text editor and open the password file of bandit26 using the file opening command within the VIM text editor. We are able to open this password file containing the bandit26 password because we have logged into the bandit26 account and this is right before the “exit 0” portion of the code boot us out from the machine.
The password to gain access to the next level is 5czgV9L3Xx8JPOyRbXh6lQbmIOWvPT6Z. However, level 27 is not up yet, therefore level 26 is the final bandit challenge as of now.