In level 8, we are being prompted to download a file called “app.exe” – seems like there is no other choice other than downloading it then.
To be honest, I don’t know what to do with this executable (EXE) file at first also. However, after doing some reading, I learnt a little about reverse engineering and malware analysis. However, thankfully, in this exercise, we don’t have to do all that.
Before we get started, let’s take a look at the different tools which you can use to examine an EXE file,
- Debugger: view and/or perform step-through on the running state of a program interactively
- Disassembler: transform the machine code into a human readable mnemonic representation called assembly language
- Decompiler: revert the process of compilation and turn a program into a structured higher-level language
In this exercise, we just need a debugger. There are several debuggers in the market, such as OllyDbg or WinDbg, both of them are free.
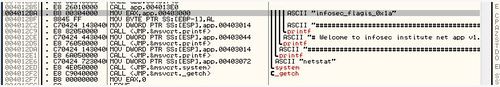
Personally, I prefer to use OllyDbg. This exercise is really simple. All you need to do is open up the “app.exe” file in your OllyDbg program and run it in debug mode (click on “play” button on the top).
There, you see the flag written in ASCII right at the very first line of the program – the flag is “infosec_flagis_0x1a”
Back to write-up list for InfoSec Institute CTF #1: Hacking for n00bz