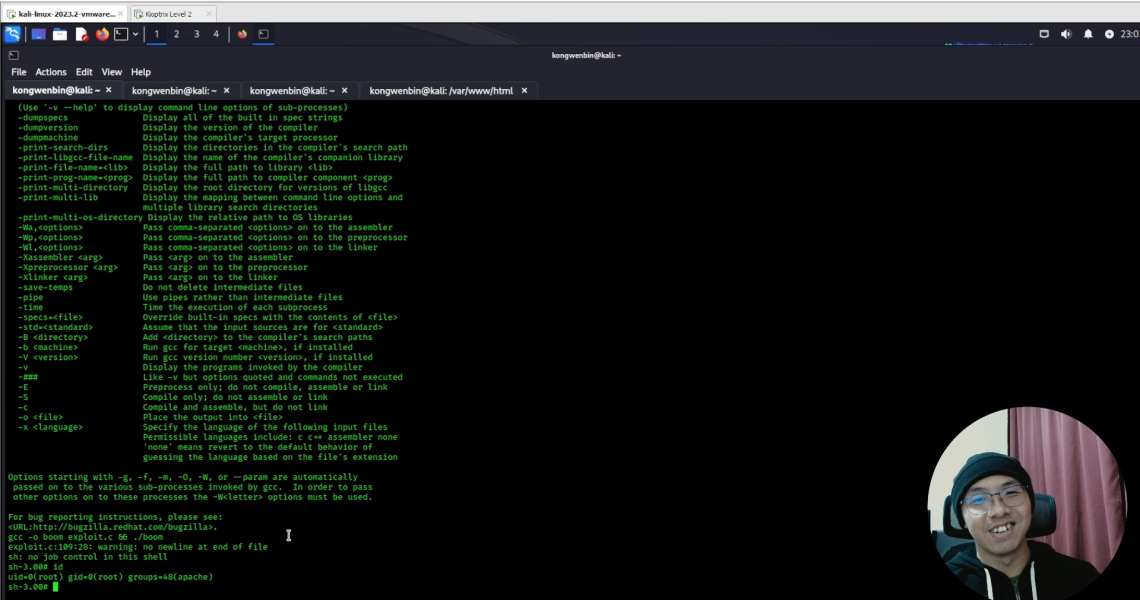
📔 This is the 3rd and FINAL video of the 3-part series for 9 tips to writing good bug bounty report! I came up with these report writing tips after reviewing over 1000 bug bounty reports. 🐞
📽️ In this video, I went through the final 3 of the report writing tips and shared some personal insights and examples, I hope they are useful to you 😊